Using AntiXss As The Default Encoder For ASP.NET
This is the third in a three part series related to HTML encoding
blocks, aka the <%: ... %> syntax.
- Html Encoding Code Blocks With ASP.NET 4
- Html Encoding Nuggets With ASP.NET MVC 2
- Using AntiXss as the default encoder for ASP.NET
Scott Guthrie recently wrote about the new <%: %> syntax for HTML encoding output in ASP.NET 4. I also covered the topic of HTML encoding code nuggets in the past as well providing some insight into our design choices for the approach we took.
A commenter to Scott’s blog post asked,
Will it be possible to extend this so that is uses libraries like AntiXSS instead? See: http://antixss.codeplex.com/
The answer is yes!
ASP.NET 4 includes a new extensibility point which allows you to replace the default encoding logic with your own anywhere ASP.NET does encoding.
All it requires is to write a class which derives from
System.Web.Util.HttpEncoder and register that class in Web.config
via the encoderType attribute of the httpRuntime element.
Walkthrough
In the following section, I’ll walk you through setting this up. First, you’re going to need to download the AntiXSS library which is at version 3.1 at the time of this writing. On my machine, that dropped the AntiXSSLibrary.dll file at the following location: C:\Program Files (x86)\Microsoft Information Security\Microsoft Anti-Cross Site Scripting Library v3.1\Library
Create a new ASP.NET MVC application (note, this works for *any* ASP.NET application). Copy the assembly into the project directory somewhere where you’ll be able to find it. I typically have a “lib” folder or a “Dependencies” folder for this purpose. Right clicke on the References node of the project to add a reference to the assembly.
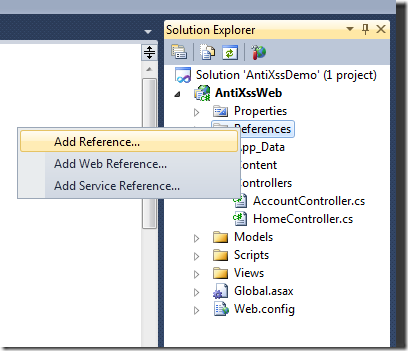
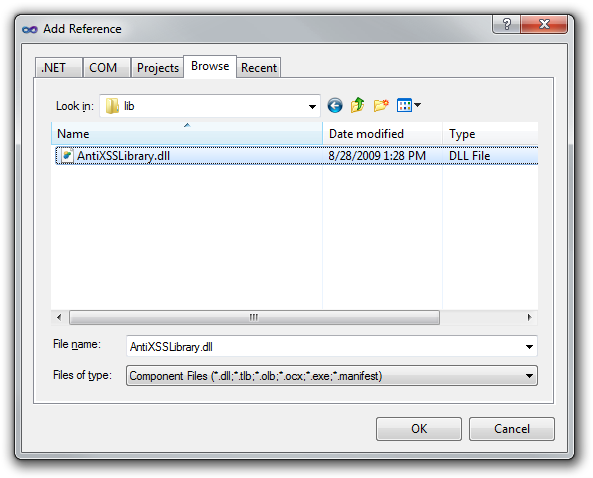 The
next step is to write a class that derives from
The
next step is to write a class that derives from HttpEncoder. Note that
in the following listing, some methods were excluded which are included
in the project.
using System;
using System.IO;
using System.Web.Util;
using Microsoft.Security.Application;
/// <summary>
/// Summary description for AntiXss
/// </summary>
public class AntiXssEncoder : HttpEncoder
{
public AntiXssEncoder() { }
protected override void HtmlEncode(string value, TextWriter output)
{
output.Write(AntiXss.HtmlEncode(value));
}
protected override void HtmlAttributeEncode(string value, TextWriter output)
{
output.Write(AntiXss.HtmlAttributeEncode(value));
}
protected override void HtmlDecode(string value, TextWriter output)
{
base.HtmlDecode(value, output);
}
// Some code omitted but included in the sample
}
Finally, register the type in web.config.
...
<system.web>
<httpRuntime encoderType="AntiXssEncoder, AssemblyName"/>
...
Note that you’ll need to replace AssemblyName with the actual name of your assembly. Also, in the sample included with this blog post, AntiXssEncoder is not in any namespace. If you put your encoder in a namespace, you’ll need to make sure to provide the fully qualified type name.
To prove that this is working, run the project in the debugger and set a breakpoint in the encoding method.
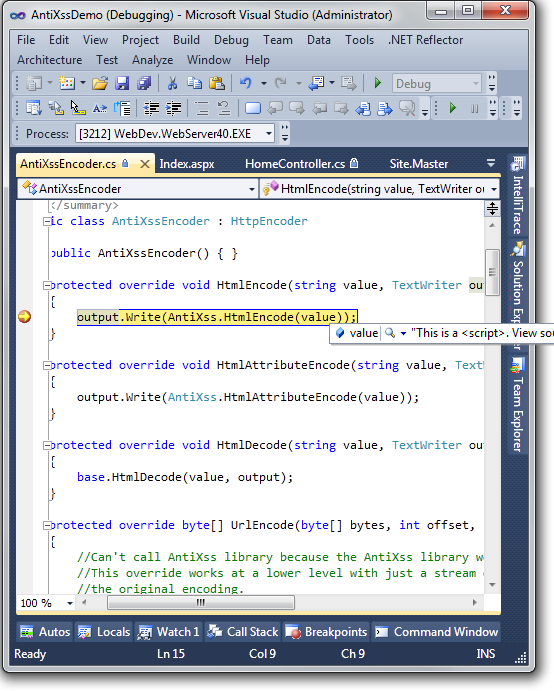
With that, you are all set to take full control over how strings are encoded in your application.
Note that Scott Hanselman and I gave a live demonstration of setting this up at Mix 10 this year as part of our security talk if you’re interested in watching it.
As usual, I’ve provided a sample ASP.NET MVC 2 project for Visual Studio 2010 which you can look at to see this in action.
Comments
25 responses